 A security vulnerability has been disclosed in the popular WordPress plugin Essential Addons for Elementor that could be potentially exploited to achieve elevated privileges on affected sites. The issue, tracked as CVE-2023-32243, has been addressed by the plugin maintainers in version 5.7.2 that was shipped on May 11, 2023. Essential Addons for Elementor has over one million active installations.
A security vulnerability has been disclosed in the popular WordPress plugin Essential Addons for Elementor that could be potentially exploited to achieve elevated privileges on affected sites. The issue, tracked as CVE-2023-32243, has been addressed by the plugin maintainers in version 5.7.2 that was shipped on May 11, 2023. Essential Addons for Elementor has over one million active installations.
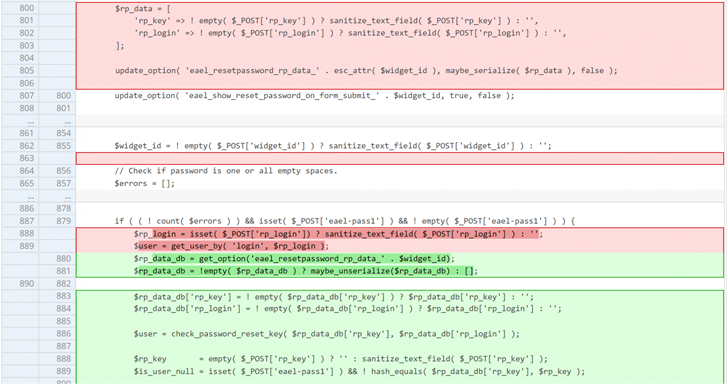
According to Patchstack researcher Rafie Muhammad, "This plugin suffers from an unauthenticated privilege escalation vulnerability and allows any unauthenticated user to escalate their privilege to that of any user on the WordPress site." Successful exploitation of the flaw could permit a threat actor to reset the password of any arbitrary user as long as the malicious party is aware of their username. The shortcoming is believed to have existed since version 5.4.0.
This can have serious ramifications as the flaw could be weaponized to reset the password associated with an administrator account and seize full control of the website.
The disclosure comes more than a year after Patchstack revealed another severe flaw in the same plugin that could have been abused to execute arbitrary code on compromised websites.
The findings also follow the discovery of a new wave of attacks targeting WordPress sites since late March 2023 that aims to inject the infamous SocGholish (aka FakeUpdates) malware.
SocGholish is a persistent JavaScript malware framework that functions as an initial access provider to facilitate the delivery of additional malware to infected hosts. The malware has been distributed via drive-by downloads masquerading as a web browser update.
The latest campaign detected by Sucuri has been found to leverage compression techniques using a software library called zlib to conceal the malware, reduce its footprint, and avoid detection.
"Bad actors are continually evolving their tactics, techniques, and procedures to evade detection and prolong the life of their malware campaigns," Sucuri researcher Denis Sinegubko said.
"SocGholish malware is a prime example of this, as attackers have altered their approach in the past to inject malicious scripts into compromised WordPress websites."
It's not just SocGholish. Malwarebytes, in a technical report this week, detailed a malvertising campaign that serves visitors to adult websites with popunder ads that simulate a fake Windows update to drop the "in2al5d p3in4er" (aka Invalid Printer) loader.
"The scheme is very well designed as it relies on the web browser to display a full screen animation that very much resembles what you'd expect from Microsoft," Jérôme Segura, director of threat intelligence at Malwarebytes, said.
The loader, which was documented by Morphisec last month, is designed to check the system's graphic card to determine if it's running on a virtual machine or in a sandbox environment, and ultimately launch the Aurora information stealer malware.
The campaign, per Malwarebytes, has claimed 585 victims over the past two months, with the threat actor also linked to other tech support scams and an Amadey bot command-and-control panel.
Essential Addons for Elementor Plugin Flaw Actively Exploited
Wordfence, in its own advisory, said the critical vulnerability in the Essential Addons for Elementor plugin is being actively exploited in the wild, and that it blocked 200 attacks targeting the flaw in the past 24 hours, making it imperative that users move quickly to update to the latest version.











No comments:
Post a Comment